Countermeasure to Structured Query Language Injection Attack for Web Applications using Hybrid Logistic Regression Technique
Keywords:
Database Management System, Logistic Regression, SQL Injection AttackAbstract
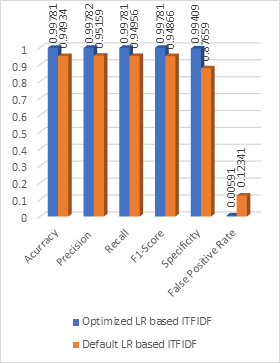
The new generation of security threats has been promoted by real-time applications, where several users develop new ways to communicate on the internet via web applications. Structured Query Language injection Attacks (SQLiAs) is one of the major threats to web application security. Here, unauthorised users usually gain access to the database via web applications. Despite the giant strides made in the detection and prevention of SQLiAs by several researchers, an ideal approach is still far from over as most existing techniques still require improvement, especially in the area of addressing the weak characterisation of input vectors which often leads to low prediction accuracy. To deal with this concern, this paper put forward a hybrid optimised Logistic Regression (LR) model with Improved Term Frequency Inverse Document-Frequency (ITFIDF-LR). To show the effectiveness of the proposed approach, attack datasets is used and evaluated using selected performance metrics, i.e., accuracy, recall, specificity and False Positive Rate. The experimental results via simulation when compared with the benchmarked techniques, achieved performance record of 0.99781 for accuracy, recall and F1-score as well as 0.99782, 0.99409 and 0.00591 for precision, specificity and False Positive Rate (FPR) respectively. This is an indication that the proposed approach is efficient and when deployed is capable of detecting SQLiA on web applications.
Published
How to Cite
Issue
Section
Copyright (c) 2022 Shehu Magawata Shagari, Danlami Gabi, Nasiru Muhammad Dankolo, Noah Ndakotsu Gana

This work is licensed under a Creative Commons Attribution 4.0 International License.





